 Â Â Â
  Â
With the continuous development of network technology, a series of network malware has been continuously derived. Ransomware is a type of malicious software that hackers use to hijack user assets or resources and use them as a condition to extort money from users. The very hot CryptXXX has changed recently, and the new version of CryptXXX has become even fiercer.
Temporarily no solutionThe new version of CryptXXX ransomware not only encrypts all files on the target user's computer and network, but users can't yet restore files with data backup - this is one of the important feature upgrades of the new CryptXXX.
Kaspersky Lab’s security researchers have been fighting CryptXXX: Previous researchers have released a decryption tool that allows victims to recover their files without having to pay a ransom; if there is no decryption tool, the victim needs at least Pay $500 to decrypt the file. Developers of CryptXXX discovered that after Kaspersky's move, they also began to adjust program code to make the cracking process more difficult. Recently developers released a new version of CryptXXX. In a blog on Monday, security firm Sentinel One mentioned that between June 4 and June 21, the total amount of ransom in the new version has reached $45228, which of course does not include the revenue of the previous version.
Actually as early as May 21, the developers of CryptXXX updated the malware code to version 3.0. The purpose of this update is to prevent Kaspersky’s RannohDecryptor decryption program from unlocking encrypted files for free.
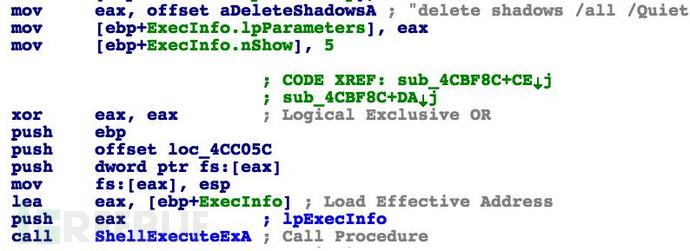
The new version of CryptXXX still supports the encryption of individual files, but the file size is limited to 512KB. The main improvement of the new version is that the difficulty of cracking has increased a lot. other improvements include the fact that the new CryptXXX suffixes for encrypted files are uniformly .crypt1, compared to the previous .crypz and .crypt suffixes; and, as mentioned earlier, the removal of shadow volume backups for the system prevents data from being restored from backups. . In addition, the spread was carried out through spam, but SentinelOne said that hackers may also use other methods of transmission.
New version of CryptXXX analysisView malicious DLL file attributes and find that its file attribute details actually come from a legitimate file named _BigBang.dll. The details of the two are basically the same.


In fact, from the details of such documents, we can't see any difference at all, making it look like a normal program. The previous CryptXXX sample also disguised as Microsoft's legitimate DLL file. Judging from the unpacker's imports, most of the content seems to have little problem, and occasionally there are some words related to crypto encryption. Judging from the list of imports and exports, many functions are related to image processing (which is definitely not the same as the legal _BigBang.dll mentioned above). It seems that there is no use for these functions. These should be used to prevent analysis. of.
The Unpack process allocates memory for the encrypted payload through VirtualAlloc and then copies the encrypted bytes. The payload is then decrypted, but it is still compressed.

According to the experience of the previous version, you can find the "MZ" header here, but find "M8ZP8" and a part of the readable string "This ? progr3am...". This is actually normal for Windows executables. The M8ZP8 header matches the aPLiB compressed PE file.
Click here to view the Python script, which contains details of the implementation of the compression algorithm and the technical description of the operation. First dump contains the memory segment of the compressed payload, prunes null bytes, and decompresses it successfully using the above Python script. The resulting file is then analyzed with IDA, which is in fact incomplete and does not include a valid import table.
After payload is decrypted, unpacker creates the file C:\PROGRA~2\Z (c:\ProgramData\Z), which is checked by kernel32.GetFileType to check if it is FILE_TYPE_CHAR. If so, the code ends without executing a malicious payload. Subsequently, the current time, file name, plus, is written into the Z file. Like this:

Shortly after these strings are written to the file, the file will be deleted. It is not clear why this is done, it may be used to interfere with the analysis process.
Then unpaker checks the registry to confirm the location of Startup:
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders\Startup
C:\Users\
The role of this position is actually very clear, Unpack code will be placed in the HTML ransom letter, which is also the focus of extortion process thing.
From the analysis of the sample, it is executed from a .Ink shortcut that points to rundll32.exe F0F3.tmp.dll, MSX3. Here, behind, MSX3 is an additional parameter, this command is to load F0F3.tmp.dll, then execute the MSX3 function. In fact there is no MSX3 function inside the unpacker, so it should be part of the payload.
Therefore, it is very possible to dump the unpacked payload by calling VirtualProtect. Now that we need to confirm the address of the MSX3 function, I create a breakpoint in GetProcAddress.

After retrieving the address of MSX3, the execution jumps to this address, and the file encryption and extortion behavior begins.
It seems that the payload was compiled using Delphi, as can be seen from the following information. From the following list, some imports also seem to use the DNS, POP3, and SMTP protocols. However, these functions should be invoked through different entry points than MSX3.

Finally, the files locked by ransomware are mixed using RSA and RC4 encryption. The encrypted file extension is .cryp1, and the previous version has the extension .crypt. As mentioned earlier, the previous version can be decrypted by the decryption tool, but the new version cannot be realized.
There is a ransom note in each folder where the encrypted file is located. One of them is a text file and the other is HTML. Text ransom letters are as follows:

The new features introduced in the new CryptXXX mentioned above: After the file is encrypted, all backup files on the disk will be deleted, preventing users from using files to recover this trick.
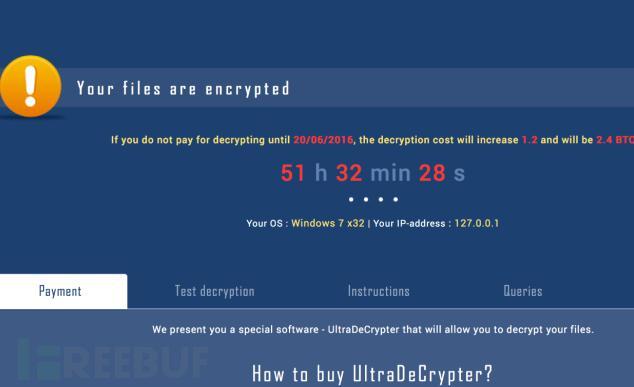
The ransom information displayed on the screen looks like this:

In order to further warn users of the seriousness of the problem, CryptXXX will also be

Path, create
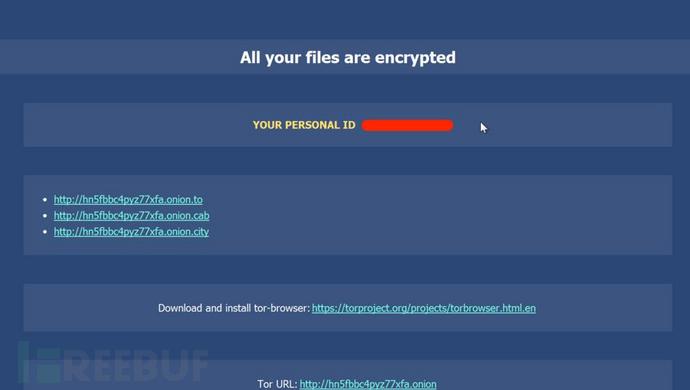
Click to enter the payment page, the page will let the victim fill in the corresponding information, is the ID of the ransomware distribution:
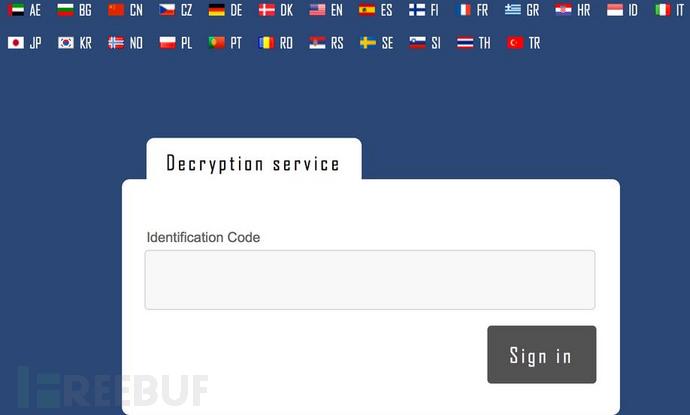
After logging in with this ID, the following page is displayed:
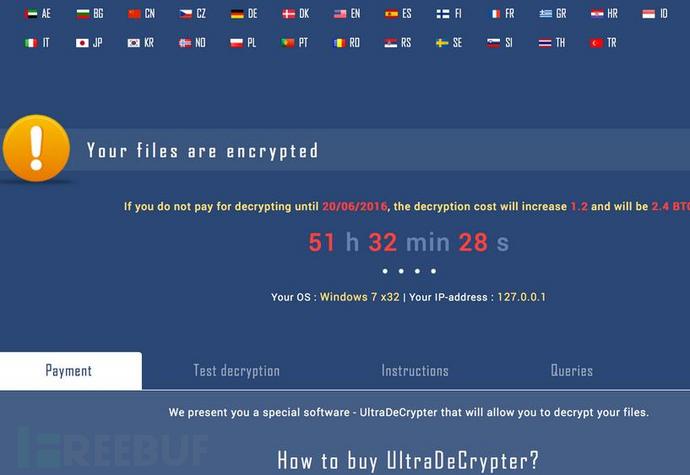
If the victim hasn't heard Bitcoin or won't pay with Bitcoin, then it doesn't matter. The following page will teach you how to do it.
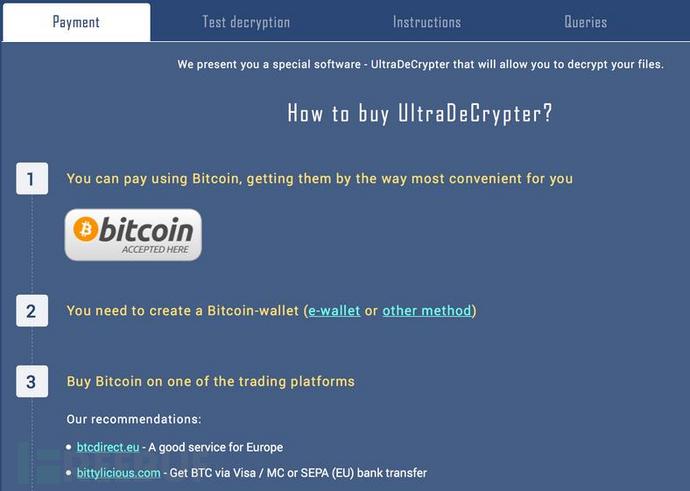
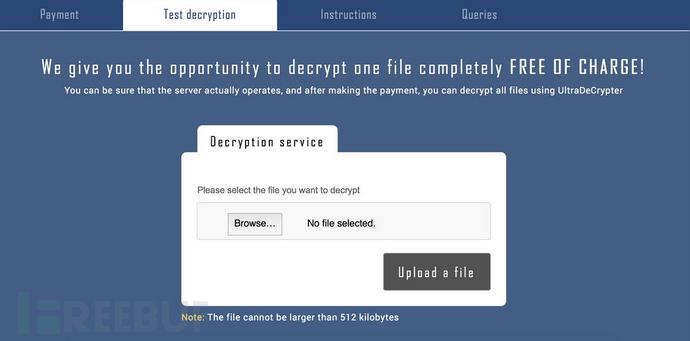
In order to prove that they can indeed provide decryption services, the following page is mainly for the victim to try the decryption service (the service is very intimate), but this so-called trial service, the size of the decrypted file is limited to 512KB.
In fact, to avoid ransomware infection, just as to avoid other malware. Keeping Windows and browser related components (Java, Adobe, etc.) get the latest updates. In addition, we must keep the browser clean, pay attention to the prevention of intrusion of adware that can lead to malicious infections, and do not easily open e-mail attachments of unknown origin. This new version of CryptXXX has the ability to delete shadow volume backup files from the disk. In fact, you can also consider backing up important files to other locations.
Lei Feng Net Note: This article reference sources: arstechnica, sentinelone, compiled by rice ball Jun, FreeBuf exclusive article authorized Lei Feng network (search "Lei Feng network" public number concerned) release, please indicate the source (FreeBuf hacker and geek FreeBuf.COM) .
Toy Sound Module, Musical Module for Toys, Waterproof Sound Module
AST Industry Co.,LTD , https://www.astsoundchip.com